Tomato Firmware OpenVPN Setup
Last updated by Andrew Mcleod on July 26, 2021 18:46
For pre-configured VPNSecure DD-WRT or Tomato based routers please purchase a router from Flashrouters.com
This guide will walk you through the process of configuring your Tomato Firmware based router to connect to our OpenVPN servers.
It has been written to work for the Linksys E2000 router running Tomato USB build "E2000 VPN" version 1.28, but it will work for other versions with minimal modifications.
Step 1) Get your OpenVPN keyfiles and server configurations
The first thing you will need is your OpenVPN keyfiles and certificates - these are emailed to you in a .zip file when you first purchase an OpenVPN plan, and can also be requested from our members area at any time by clicking the blue "Regenerate OpenVPN keys" button.
Extract this zip file somewhere handy, as you will need the contents of the "yourusername.crt", "yourusername.key" and "ca.crt" files in a few moments.
You can request the server configuration files by logging into the members area and clicking "Generate server configs".
Step 2) Remove password protection from your keyfile
By default the OpenVPN keyfiles we generate are protected by a "key password" - but the Tomato firmware is unable to decrypt them automatically, so we need to remove this layer of password protection.
There are a few options for removing this protection, depending on your level of technical knowhow and available resources:
a) Contact Support Staff: We can remove the password for you and send you an unencrypted file. Contact us by email or live chat
b) Decrypt using OpenSSL on linux: The command "openssl rsa -in username.key -out username.keyout" will ask for your password, then put the unprotected key in username.keyout.
c) Decrypt using Tomato firmware: Login to the router web interface, click Tools > System and paste the following command into the interface:
<em>cat >/tmp/home/root/tempkey <<'EOT'<strong>CONTENTS OF YOUR USERNAME.KEY HERE</strong></em>
Then press execute to save your protected keyfile to the router temporarily. The following command will decrypt the keyfile and display the unencrypted key back in the web interface ready to be copied into a text editor for later:
<em><em>openssl rsa -in /tmp/home/root/tempkey -out /tmp/home/root/tempkeyunprotected -passin pass:<strong>YOURPASSWORD</strong> && cat /tmp/home/root/tempkeyunprotected</em></em>
Step 3) Configure the router:
Login to the web administration interface of the router and click "VPN Tunnelling" , "Client" and "Basic".
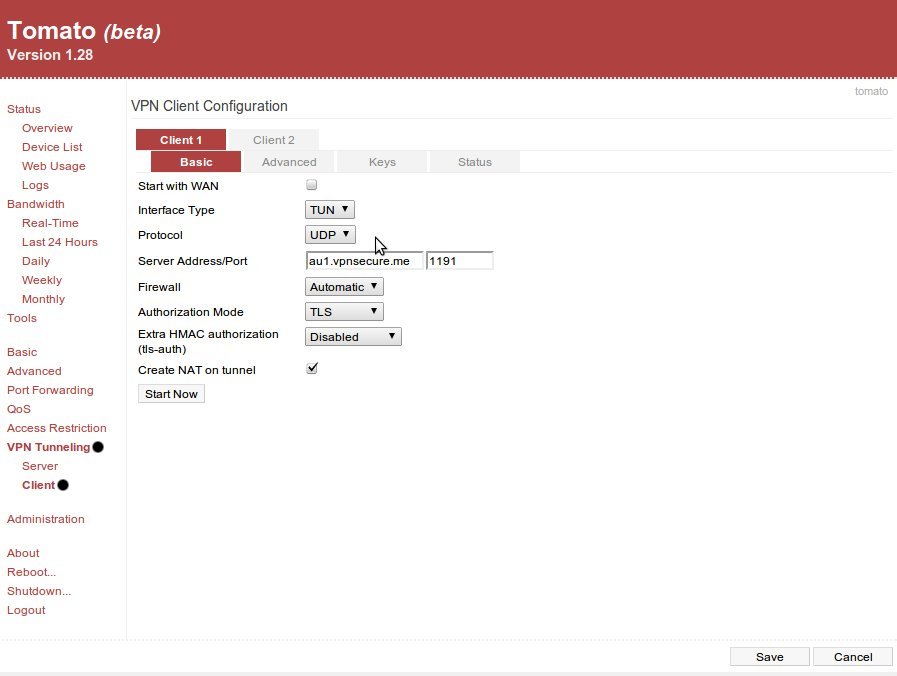
You can find the specific server settings you require inside the server settings .zip you requested earlier. The only settings that are unique to each server are the Protocol, Address and Port. These are the settings required to connect to our Australian server. Click "Advanced".
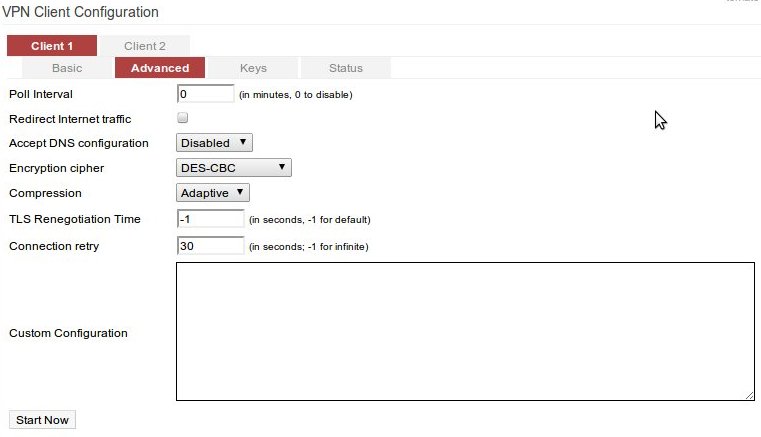
The main setting to focus on is changing the Encryption Cipher, to DES-CBC.
Additionally, you may find your device does not support IPv6, in which case the following lines must be added to the "Custom Configuration" text box:
#start
pull-filter ignore "ifconfig-ipv6"
pull-filter ignore "route-ipv6"
# end
Next, click the "Keys" tab.
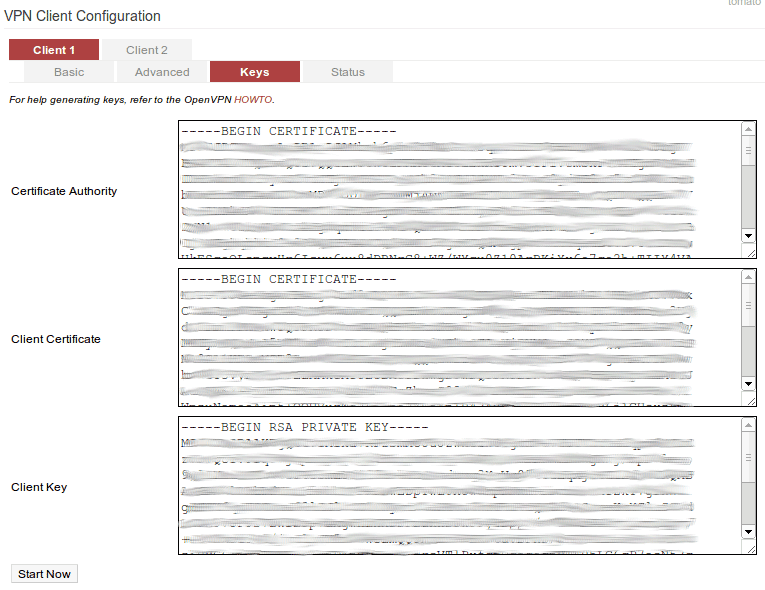
On this screen you need to paste in the contents of the OpenVPN authentication files you requested earlier.
Certificate Authority: Is named "ca.crt"
Client Certificate: Is named "yourusername.crt"
Client Key: Is the unencrypted keyfile you created in step 2 above.
At this point you just need to click "Save" and "Start" and it should just work :)
VPNSecure Provides Secure VPN servers in over 45+ Countries
If you are a looking for a versatile easy to use VPN service, checkout Today
